Malware Creators Adapt to New SHA-2 Certificate Technologies to Thwart Security Measures
April 13, 2016
It’s a constant battle between the good guys and bad guys. The good guys are transitioning to the stronger SHA-2 certificates on websites, so the bad guys are now using stolen SHA-1 and SHA-2 certificates.
Symantec noted in a recent blog that these stolen certificates are being used in an attempt to thwart the new browser technology that will indicate if a site is using the outdated SHA-1. In fact, they are using both versions so that older websites will detect the older certificate and newer ones will detect the newer certificate. That’s pretty crafty of them.
They are doing this so that the malware can bypass security measures put in place. Symantec found that a version of the Carberb.B Trojan was modified to use exactly this approach. This malware uses an infected attachment in email with a subject of ATTN 00890 and targets those who work in accounting departments. The macro embedded in the attachment downloads a malicious .exe file from a server in the island nation of Mauritius off the coast of Africa.
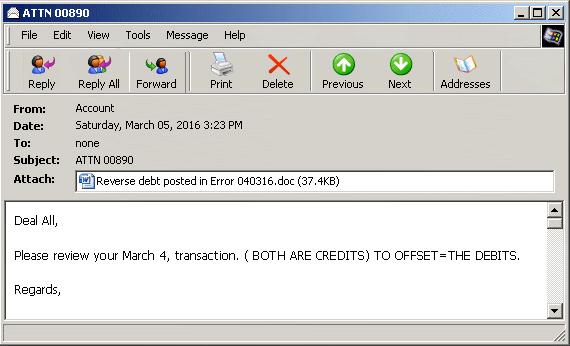
This scenario shows how malware creators are adapting and using legacy systems to wreak havoc. So, those who are still running the unsupported Windows XP in their organizations should make a serious effort to upgrade. In addition, make sure all patches are applied as soon as they are released. This should be part of a comprehensive security strategy.
However, because this effort by the malware creators is still new, US companies have been given a window of time to address this specific attack. The window is not big so action should be taken.
© Copyright 2016 Stickley on Security

