Healthcare Industry Sick With Internal Data Breaches
February 2, 2018
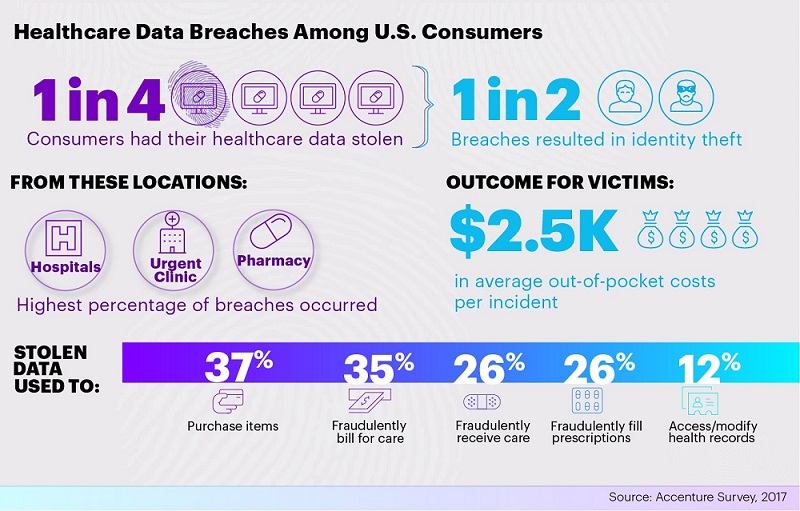
In 2017, hospitals and health insurers comprised an alarming number of data breaches. They found their data systems hit by all types of ransomware, viruses, and other malware. Outside hacks are bad enough, but when it’s an inside job the stakes are even higher.
A major struggle for the healthcare industry is terminating access for ex-employees to data systems. Policies and swift action are needed for preventing former employees from doing damage not only to systems, but also to unsuspecting patients and subscribers. In November of last year, the Department of Health and Human Services addressed the threat, suggesting critical precautions for employers to take.
- Notify IT departments about a planned or unplanned employee dismissal. That should set into action the process of denying access to servers and other electronic data. Accounts should be immediately deactivated, deleted, and/or passwords changed.
- Terminate physical access as soon as possible. Change security codes, door locks, and other means of access that a former employee may have.
- Have all work-related devices like keys, ID badges, smart phones, or laptops given to employees physically secured or immediately changed or deactivated.
- Terminate all remote access to the company website, email, social media, and cloud-based abilities. Be aware of any and all means of access an employee may be given. Keep records of an individual’s privileges to different levels of ePHI.
- Regularly audit security policies and means of employee access to data to ensure the latest security patches and updated and improved policies are implemented.
- Keep a checklist for all tasks that need to be completed upon an employee's departure, regardless of the reason for the exit.
Protected Health Information (PHI or ePHI for electronic data) is key to keeping all that data safe from harm. By spending some time recording employees’ access, you can quickly mitigate your risk when someone departs.
© Copyright 2018 Stickley on Security

