New Mobile Malware Bypasses Two Factor Authentication
April 8, 2016
We have heard of mobile apps that steal banking credentials before. We have even somewhat recently heard of one that targets large banks (Xbot). However, a newly discovered one that is making the rounds and is likely soon making a debut in the United States. It uses Flash Player to trick Android users and can even bypass multi-factor authentication methods.
The malware uses a very legitimate-looking Flash Player icon and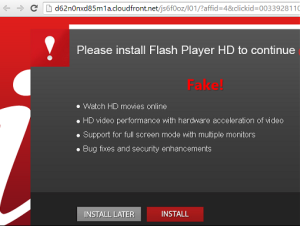 targets a list of the largest 20 banks in the aforementioned countries. The servers it uses were registered in January and February of 2016 and the URL paths they are using are regenerated hourly. This is likely to avoid detection by anti-virus software products. However, some of these products are indeed catching them.
targets a list of the largest 20 banks in the aforementioned countries. The servers it uses were registered in January and February of 2016 and the URL paths they are using are regenerated hourly. This is likely to avoid detection by anti-virus software products. However, some of these products are indeed catching them.
It is common advice now that everyone should install anti-malware apps on all devices that interact on the Internet in any way. This includes mobile devices, laptops, and desktop computers. Remember to make sure they are updating regularly. If there is an option to do automatic updates, it is recommended that it is active. Even if they are known to miss some, they catch far more than they miss.
There are many products for this and some are inexpensive or even free. However, do research to make sure they are legitimate and from trusted companies before downloading anything. A good way to do this is to check reviews in the app store. Keep in mind that if there are only a few reviews and they are all good or glowing, it’s worth it to do extra reading elsewhere to make sure they are real reviews.
Avoid downloading apps from locations other than the official app stores. Doing this, otherwise known as sideloading, adds risk of executing malware of some type onto your device. Although it isn’t 100% guaranteed that you won’t get a bad app in the stores, the likelihood is significantly lower because in order to get apps into those stores, there are more stringent security requirements for the products.
This particular piece of malware will ask for administrator rights. Once they are provided the app communicates with a remote server about details of the device. If there are matches of the banking apps, the app launches a fake login screen and any data that is entered is sent off to the remote server. If multi-factor authentication security is active on the account, the text message gets intercepted by the remote server and is therefore thwarting that extra security check. However, it’s still advised to activate any multi-factor authentication offered by your financial institution. More often than not, this will prevent such malware from taking up residence on your devices.
One giveaway that this app is fake, is that it asks for administrator rights. Never give these. There are very few, if any apps that need this and Flash Player certainly does not. If this access is given to someone with ill intentions, they can do a lot of damage. If in doubt, say “no.”
Also, Adobe no longer supports Flash Player development on Android, so if an app offers that functionality, you should question it.
Fortunately, this malware-infested app can be uninstalled. It may not be easy though and if the malware has configured the device to not allow deactivation of administrator rights, it can be a real headache. This is an argument in favor of keeping regular backups of devices. Then, if something like this creeps in, you can wipe the device and restore from a backup that didn’t include the malware.
© Copyright 2016 Stickley on Security

