Hacking Scams Steal Over $12.5 Billion From Businesses
December 26, 2019
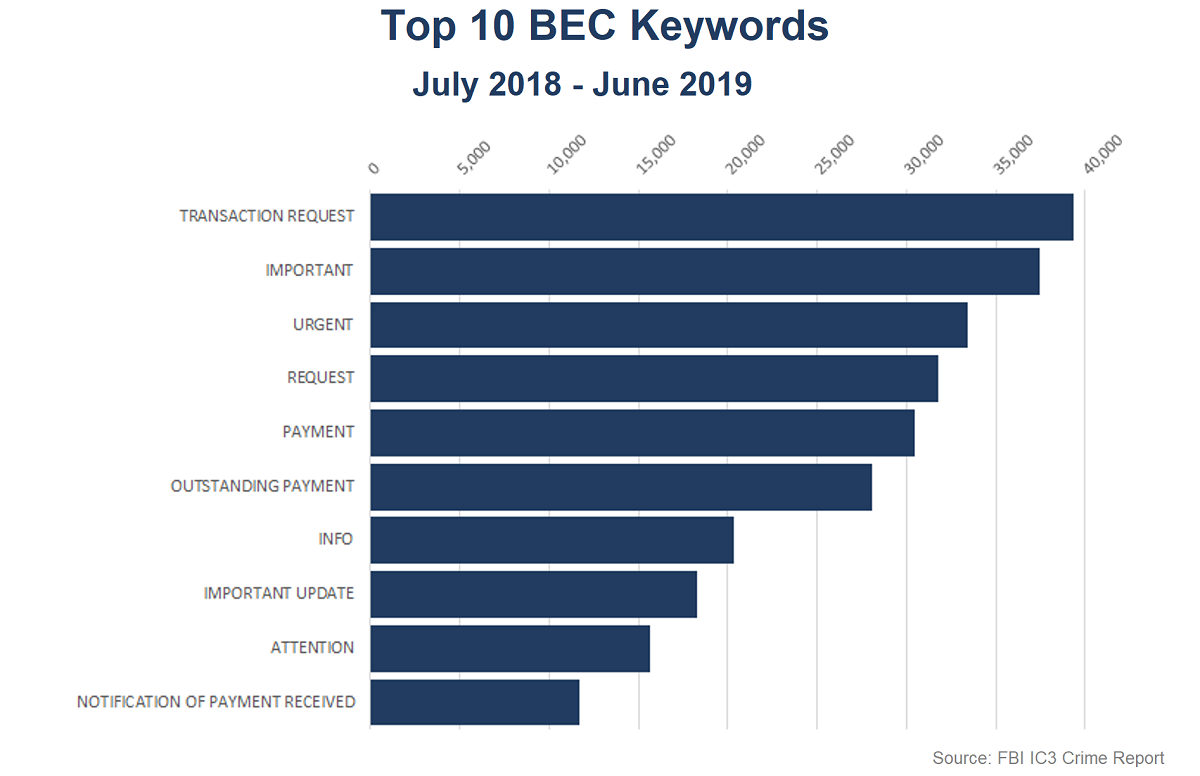
Never ones to sit still and count their stolen riches, hackers are once again finding better scams in their never-ending attacks on the business world. In late 2018, the IRS released a warning about a jump in phishing emails targeting payroll direct deposit and wire transfer scams. It’s the FBI who discovered losses totaled $12.5 billion to the business community in 2018. That’s a huge haul for scammers and according to a warning by the IRS, it’s likely only going to get worse. Unless businesses proactively educate employees and guard against the scams, it doesn’t look good.
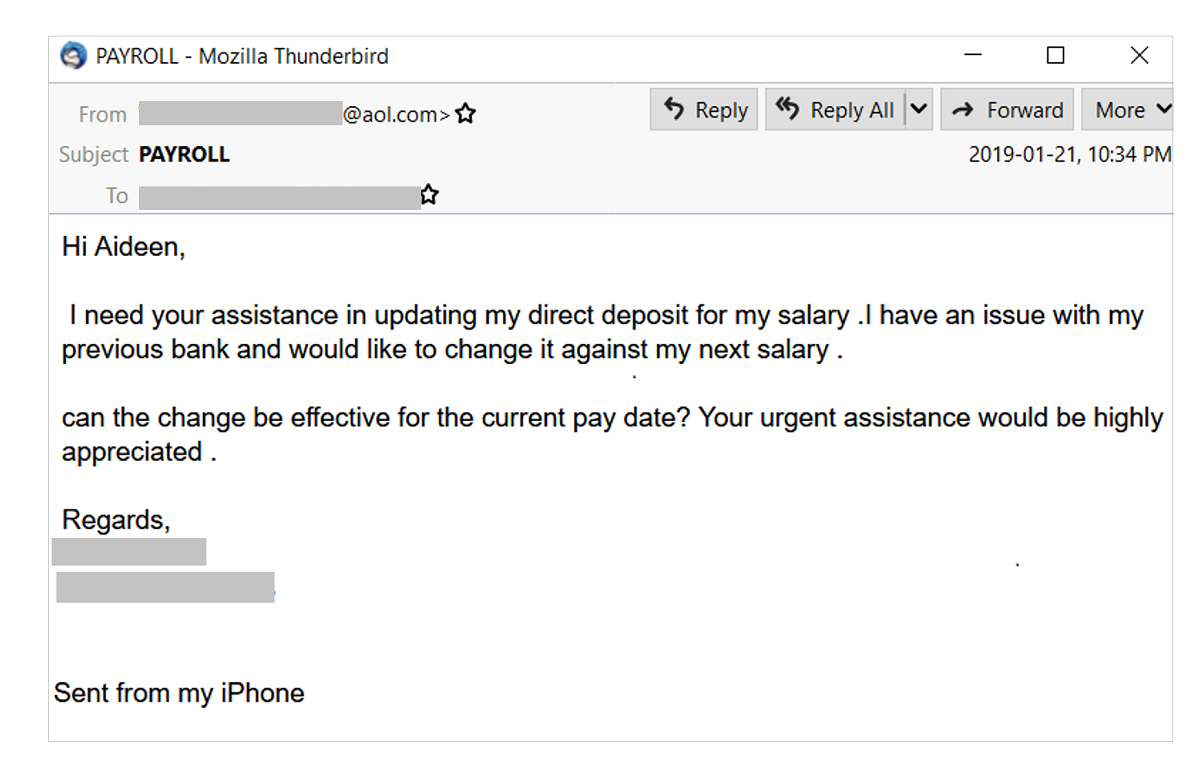
As we know, hackers are continually improving their tricks, always learning from earlier attempts. A recent scam was discovered at KVC Health Systems in Kansas City, KS, a non-profit agency for child welfare and behavioral healthcare organization. This new scam involves re-routing employee direct deposit paychecks to new accounts–ones belonging to hackers. The phony email requests were sent to Human Resources email accounts, mostly from high-ranking positions like CEO’s and CFO’s in the company. Short but sweet, the emails instructed HR employees to send their paychecks to a new account. Once done, KVC was on the hook for the pilfered paychecks and those employees affected could do nothing but wait for the problem–and their paycheck–to be resolved. Remember, if it happened here, it can happen anywhere.
It’s a new twist on a not-very-old trick. Hackers who once targeted big money fraudulent transfers are now focusing on smaller amounts with more victims. It’s quantity over quality. KVC had even implemented email filters that red flag emails with suspicious subject lines and content. The emails hackers sent slipped past the filters with simple, non-threatening messages. Employees trained to spot phishing emails were also caught off-guard.
Since cybercriminals are ramping up their tricks, employees and companies need to take extra cautionary steps. Company social media websites need to proceed with caution. Posting first and last names of employees is the start of a hacker’s email list; especially for those who post they are in HR or finance-related departments. Always have two people review and verify wire requests and always verify changes to a direct deposit account with the requestor using the phone, a new email message with an address you already know, or by paying a personal visit to his or her office. Picking up the phone is a great way and maybe the best way to start. The key to avoiding this scam is verification, and at times more than once is necessary. Someone who seems inconvenienced by verifying a request would ultimately agree that better safe than sorry is the way to go.
December 2019
Stickley on Security