Facebook Servers Deliver Malware To Steal Login Credentials
October 13, 2017
It may be difficult to understand the Facebook Content Delivery Network (CDN) and it isn’t really important that you do. But this is the way some cybercriminals are distributing malware to a large amount of unsuspecting Facebook users. The CDN is how the social media site delivers video and photos to its users. In this case, the enterprising thieves are using these servers to deliver banking Trojans to your devices that can and will steal your credentials.
The scam works like this: An email shows up in your inbox that appears to be from local authorities. Included is a link that takes you to a particular CDN. On that CDN resides the malware that executes the banking Trojan.
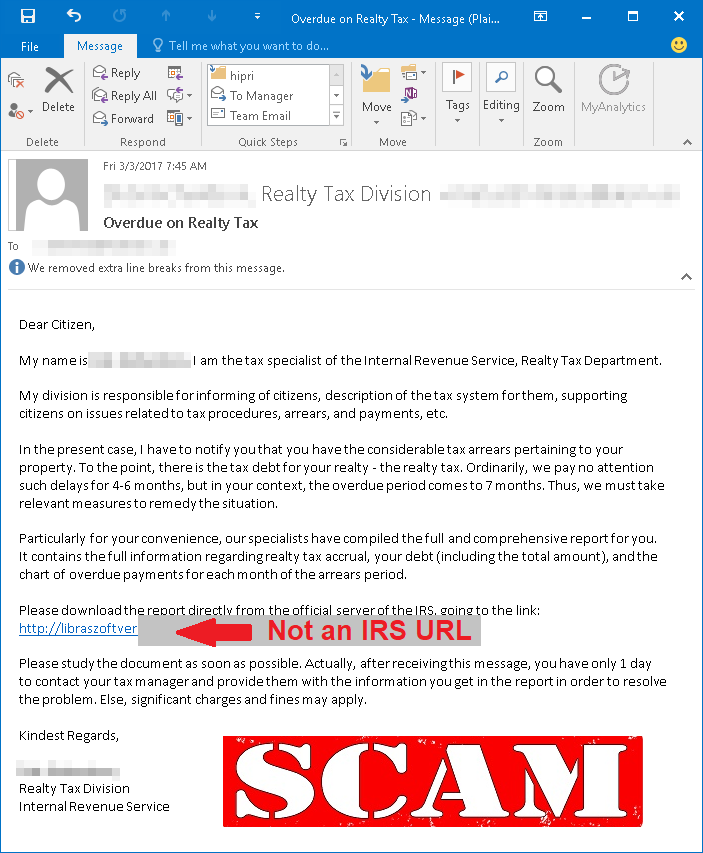
The concern here is not simply that by using these CDN servers the malware can be delivered to a large number of people quickly; it’s also a matter of trust. You see, it is largely believed among cybersecurity professionals, that the perpetrators of this scheme are the very same ones that used Dropbox and Google’s cloud storage in the same way not long ago. All of these companies are trusted within the user communities and if we cannot trust them, then who can we really trust?
The answer eludes us. In fact, since they are trusted, cybersecurity solutions that are supposed to help protect us against attacks such as these recognize their domains as “safe” and won’t see malware on them as a threat. If the criminals used a custom domain to deliver this malware, these products would immediately discover them and block their deliveries. With large companies like these, it’s not so simple to just cut access off when something like this happens.
This is why it’s really up to users to be wise when using the Internet. Keep in mind that public officials typically do not use platforms such as links in email or social media to deliver information to citizens. So if you receive a link or attachment purportedly from a government official or public servant, it should be questioned. Don’t take any quick action. Instead, try checking their public social media sites or referring to your local news publications, radio stations, and television stations directly to get the information that is supposedly contained in the links.
© Copyright 2017 Stickley on Security
October 11, 2017

