Facebook Friends Are Duping You With Malvertising
September 29, 2017
They are at it again; although they really don’t ever seem to let up either. The cybercriminals are taking advantage of “chatty” users. They are employing social engineering techniques combined with online advertising to make a lot of money. This time the vehicle of choice is Facebook Messenger. To make it an even slicker trick, they are changing what users see based on various factors, such as the operating system or browser being used.
Kaspersky Lab researchers discovered this new malvertising campaign that infects all platforms. The initial infection is via Facebook Messenger, but the researchers are not sure how the users’ information is retrieved in the first place. They suspect it could be from hijacked browsers, via clickjacking, or by using stolen credentials from separate incidents.
In any case, it works this way: A video is received that appears to be from someone on the user’s contact list. When that is clicked, other websites collect information about the user’s system such as the browser and operating system, language, geo location, etc. Then it redirects to a Google document with a dynamically generated video thumbnail. If that thumbnail is clicked, he or she is redirected again to a customized landing page displaying something different based on the browser and operating system.
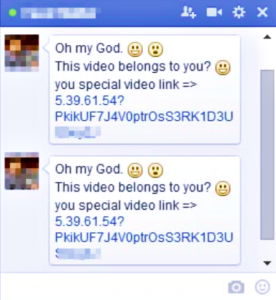 The analysts found that Firefox users saw a phony Adobe Flash Update and Google Chrome users got a video of a fake Chrome extension. Safari users saw yet something different.
The analysts found that Firefox users saw a phony Adobe Flash Update and Google Chrome users got a video of a fake Chrome extension. Safari users saw yet something different.
The lesson here is the same as watching for phishing attempts. If you receive a chat or text message unexpectedly, it should be deemed somewhat suspicious. Don’t reply to the message, but contact your Facebook friend some other way to find out what the message is all about. If they confirm that it’s OK for you to click, go ahead. Although, be aware that even links that are confirmed and seem harmless may do damage behind the scenes.
In the case of this one, it does not appear that any Trojans or other types of malware are installed when clicking through the links. It is clear, however, that whomever is behind this scam is making a lot of money on click through advertising and probably getting real access to victims’ contacts.
© Copyright 2017 Stickley on Security

