Credential Stealing For Your Holiday Season
December 12, 2018
The holidays are quickly creeping up on us. It’s a time for being thankful and giving, but it can also be a time to reflect on the scary cybersecurity term, phishing…just because holidays are often time for reflection. By now, nearly everyone has heard it and if you work in an office, you have hopefully received some sort of training or advice on how not to become your organization’s latest victim. However, no matter how often it’s mentioned or how much training received, even the most cybersecurity-aware can fall for it, if not careful.
Menlo Security released some research recently that pointed out the increasing incidents of credential phishing. This happens when an attacker sends phishing emails with the end goal to get login credentials…for something. One of the most “famous” examples of this occurred during the 2016 presidential election time when Hilary Clinton’s former campaign manager gave up his credentials when he clicked on a link in email he thought came from a colleague.
So while some worry most about their bank accounts being emptied, perhaps it is more important to worry about email credentials, or perhaps those social media logins. After all, there is a lot of valuable information in our social media accounts and those can be used to reach a lot of people, if they are taken over.
There isn’t a single group being targeted for credential phishing, according to the research. The attackers use a couple of methods and target everything from political campaigns to public agencies to anyone that may have valuable data. The methods seem to be either copying websites to make them very difficult to detect as fake, or websites that actually take over a login page. Either way, if you enter your login credentials, you give them to someone you don’t really want to have them.
Ultimately, these attacks begin with phishing email messages. These often have some specific characteristics…such as trying to scare you into doing something quickly, else suffer some consequence or simply make fabulous promises for a reward, if you just act fast. They induce fear, urgency, curiosity, or appeal to your emotions.
Phishing is getting more difficult to spot these days. The criminals are getting very good at mimicking websites and crafting messages that are so real, that even though you may not have a Netflix account, make you think you do because they are just that good.
Still, take some time to evaluate a message before clicking any link or attachment. If it comes from an unknown sender, is unexpected, tries to scare you, promises something free if you just click and enter details, or anything that has some sense of urgency or punishment claim, it’s very likely phishing.
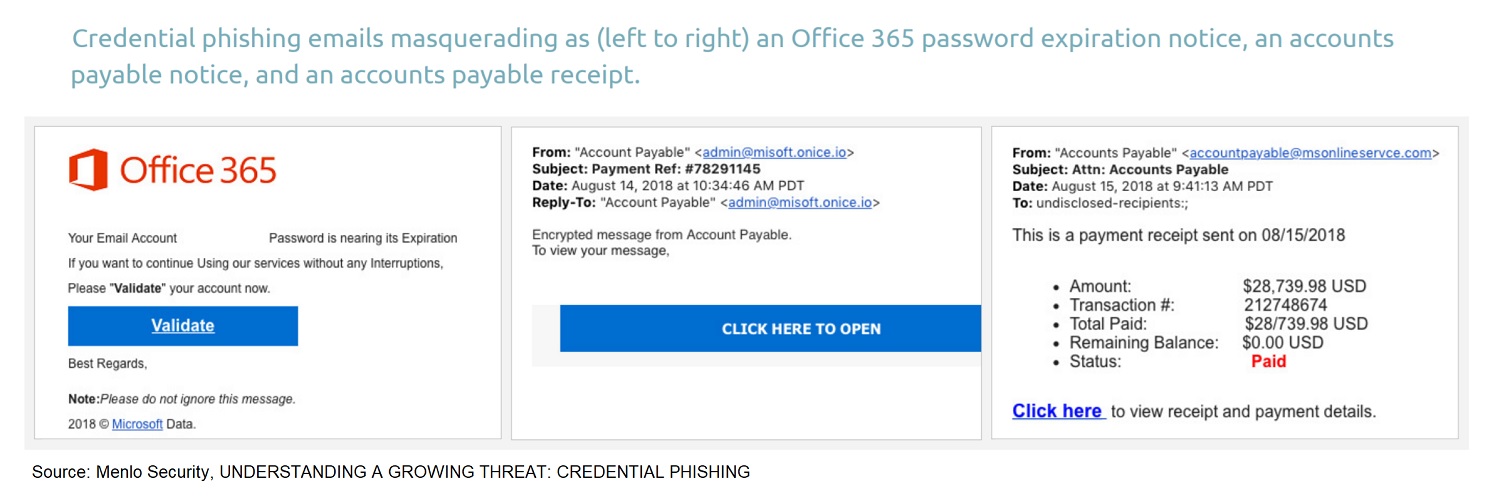
Menlo Labs found in their research that the most popular time of day for phishing to arrive in your email box is Tuesday. Be particularly cautious on that day of the week. Popular targets were Office 365 and OneDrive. Probably because people are likely to go to those places from the workplace network; and that is where the attackers really want to be. Your home network is a small treat compared to the mother lode that is the corporate network.
Remember that these attacks are not the mass spam variety. They are targeted and individualized. They are trying to get those who have the credentials to get the information the criminals really want. Often, but not always, that means those in finance and human resources departments. Be careful what information is on social media about your role at work. This can be used to construct these attacks.
So yes, sorry to break it to you, but you really are the weakest link. Tools can be put in place to scan for malware and spam, but when a message is so specific, no tool will likely detect it. At that point, security is up to you.
Stickley on Security
Published December 3, 2018

