Banking Malware On The Rise Once Again Thanks To Two Familiar Bots
August 25, 2017
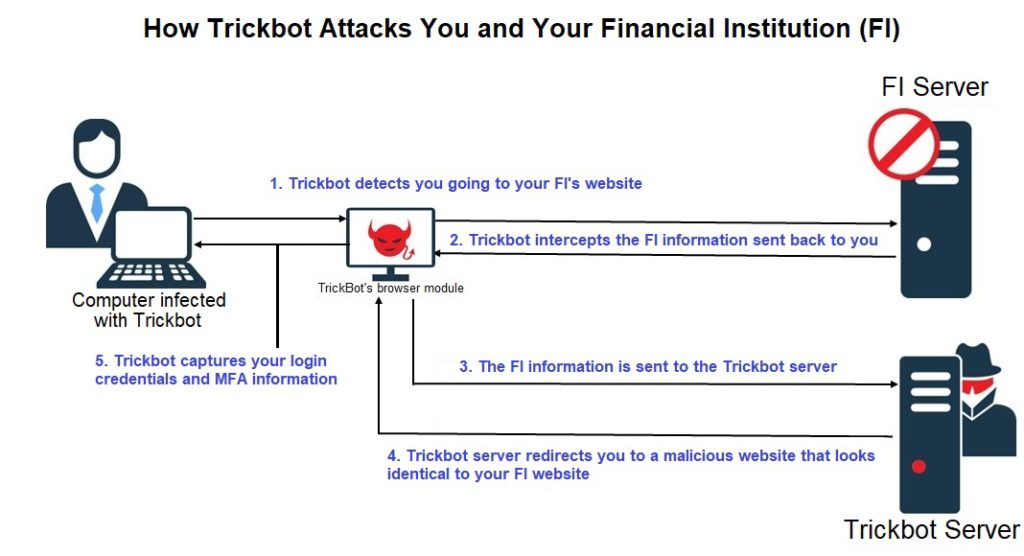
It’s being reported that while financial institutions were formerly on a downward trajectory with respect to malware attacks, it has since changed. These organizations are reporting an uptick in malware sightings and they are not limiting their targeted currencies to the traditional. Crypto-currencies are also in the crosshairs. And causing this riff are the financial industries’ biggest malicious enemies. Primarily the culprits are Trickbot and NukeBot.
Both can allow injection of malicious code into web pages that can be used to steal banking credentials and data from devices. Trickbot has been evolving of late and making its presence well known. It first is tested on lower profile targets and once those controlling it are sure it’s working the way they want it to, they go for high profile ones such as large financial institutions, wealth management firms, and wealthy individuals.
NukeBot, on the other hand, has potential to be even more dangerous. Earlier this year, the code for it was released on hacking forums. There is a lot of speculation as to who did it and why, but because the code has been made available to anyone who knows how, wants to know how, or desires to use it, there is plenty of concern that it may be even more dangerous than originally designed. In addition, because it’s still unknown as to how it is changing, whatever it does will be unexpected when it hits.
FOR HOME: Avoiding phishing and smishing scams is the simplest way to avoid being a victim of any banking malware. A link should never be clicked nor an attachment opened unless you are expecting it and know the sender. A good practice is to verify the link or attachment with the sender through a separate email or text before clicking.
Ensure you have current antivirus and anti-malware software always running on all your devices.
FOR BUSINESS: We all need to be just as safe at work as we are at home. Yes, businesses invest in network security, but phishing scams can get through the cracks every now and then so, it's important for businesses of all types and sizes to implement multiple layers of security within their networks to thwart these types of attacks. At a minimum, firewalls, as well as intrusion detection and prevention systems should be implemented. A solid anti-malware product is also needed on every machine, whether server, workstation, or mobile device.
It’s easy to forget how many employees and others hook up to a company’s network with their own devices every day. It’s worth considering integrating a “bring your own device” policy into the cybersecurity plan.
Ensure all devices, mobile or otherwise are kept updated with the latest software versions and patches and that anti-malware is installed on every single device that connects to the network.
Never forget to include a comprehensive training and awareness program in any cybersecurity plan. Humans will always be the “weakest link” when it comes to phishing attacks and it’s been determined that no matter how good anti-spam filters may be, a lot of malicious email still ends up in inboxes. Training everyone on how to spot and avoid phishing attacks can make a big difference.
In July, over a two-day period, there were two attacks that cost around $100 million in crypto-currency. Because many organizations don’t report damage from cyberattacks, it’s likely that number is much higher.
© Copyright 2017 Stickley on Security

